We’ll look at several core OAuth flows relevant to Salesforce. Join us to learn about Identity Flows OAuth 2.0.
| User interaction | No user interaction |
| Authorisation Code + Secret (Web Server) Implicit Grant (User-Agent) Authorization Code + PKCE | JWT Bearer SAML Bearer Username-Password |
Intended audience: Architects, developers, security professionals and identity buffs.
Identity Flows OAuth 2.0 For each flow, we’ll cover:
- Sequence of steps
- Interesting characteristics
- Implementation considerations and trade-offs
Common pre-requisites
- Secure HTTP channel for at least some of the communication
- Auth server provides client app for inbound integration
- Auth server client app configured with whitelist of acceptable redirect_uris (no pattern matching)
- Client aware of client_id from auth server’s client app
- Resources at client redirect_uris protect against XSS
- For mobile apps: App uses native device browser for authentication
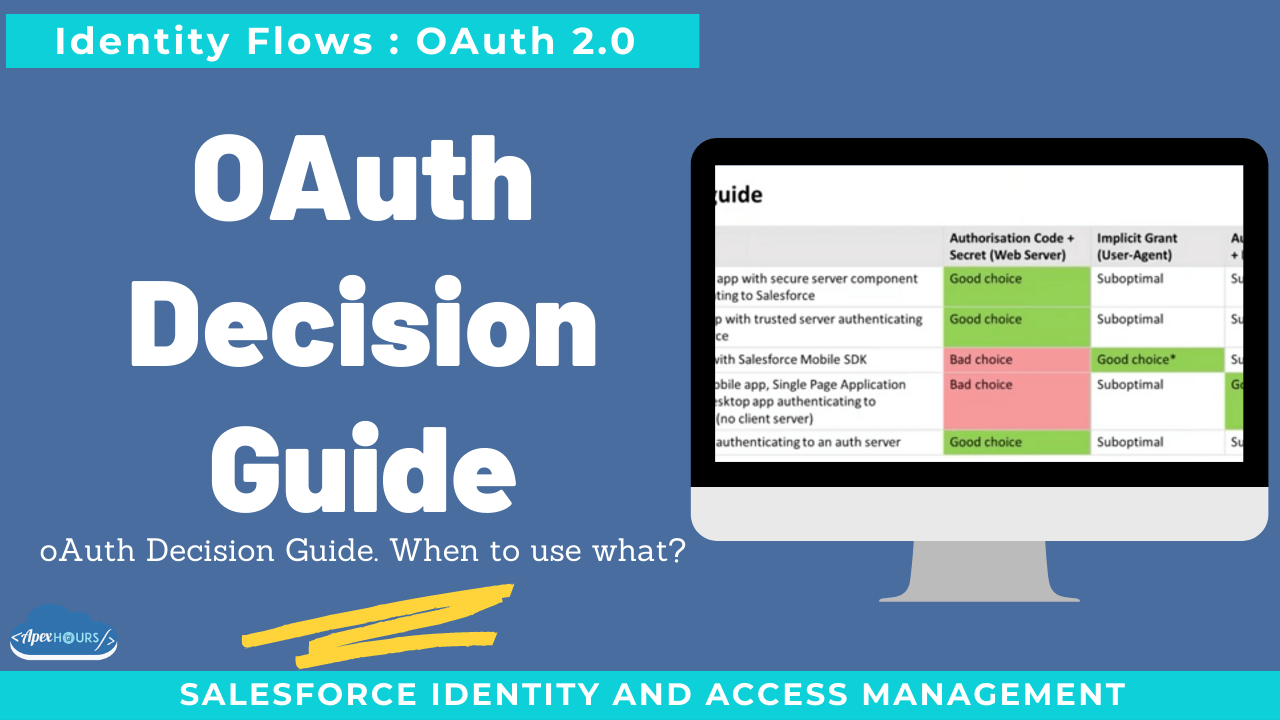
Decision guide
|
| Context | Authorisation Code + Secret (Web Server) |
Implicit Grant (User-Agent) | Authorisation Code + PKCE |
| 1 | Enterprise app with secure server component authenticating to Salesforce | Good choice | Suboptimal | Suboptimal |
| 2 | Partner app with trusted server authenticating to Salesforce | Good choice | Suboptimal | Suboptimal |
| 3 | App built with Salesforce Mobile SDK | Bad choice | Good choice* | Suboptimal |
| 4 | Custom mobile app, Single Page Application (SPA) or desktop app authenticating to Salesforce (no client server) | Bad choice | Suboptimal | Good choice |
| 5 | Salesforce authenticating to an auth server | Good choice | Suboptimal | Suboptimal |
*Assuming default Mobile SDK methods used
|
| Context | JWT Bearer | SAML Bearer | Username-Password |
| 1 | Salesforce -> Auth. Server integration | Good choice | Suboptimal | Suboptimal |
| 2 | Client Server -> Salesforce integration where client can easily construct a JSON web token | Good choice | Suboptimal | Suboptimal |
| 3 | Client Server -> Salesforce integration where client can easily construct and encode an XML format SAML assertion | Suboptimal | Good choice | Suboptimal |