If you ever wanted to publish an app on Salesforce AppExchange, you probably know of the Salesforce security review. While dreaded by many developers, it is far from an insurmountable challenge. In this session we will go over the concepts behind the AppExchange security review, what makes it so important, and how to design applications that can pass in record time.
Whether you’re a developer with an idea, a company about to launch their product on the AppExchange, or just wanted to design more secure applications, join us and understand the Salesforce security review.
What is AppExchange Security Review?
A Salesforce Security review is about building the trust between your app and clients. You can only listed your app on AppExchange after Salesforcesecurity review by adopting Salesforce best practices.
- App is reviewed by real people
- Search for security flaws
- Object, field, and record-level security
- Classes utilising ‘without sharing’
- Perform a wide variety of attacks
- Reflected XSS
- Stored XSS
- SOQL Injections
- And lots more!
- Checks for best practices
When To Take Security Into Account?
Importance of Security Review
- Are you able to identify and deflect all attack types on web platforms?
- No? Then you are reviewed by people whose job it is to detect them
- Yes? Then you know that vulnerabilities change all the time
- Your name is on the line
- Raise your hand if you know the name SolarWinds
- Keep your hand raised if you would buy from them
- Salesforce’ name is on the line
- It’s not just the right thing to do; it’s the law
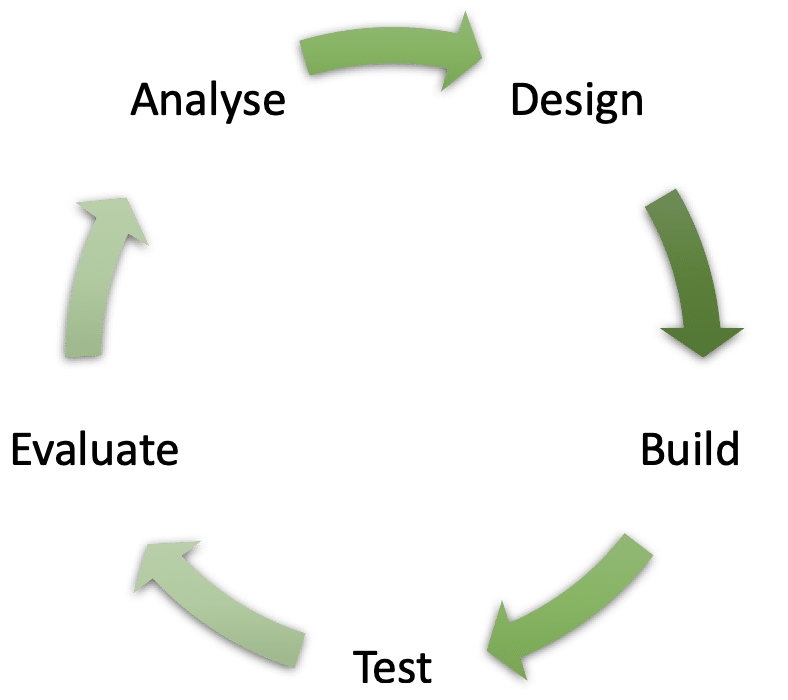
The Review Process

The Review Process
1. Registration
- ISV Registrations can take a while. Weeks, sometimes longer
- Prepare a business plan, prove it’s profitable
- Consider Salesforce’ revenue share scheme
2. PREPARATION
- Scan your code with Checkmarx
- Review review review
- Don’t review it by yourself, get second opinions
- Review and scan external services
- Heroku, S3, APIs, web apps, mobile apps, etc
- Write False Positives document
- Update technical documentation
3. SUBMIT
- Create app listing
- Prepare demo environment
- Submit for security review
- Pay the fee
4. ITERATE
- Wait 2-4 weeks
- Receive feedback
- Fix code
- Release new version
- Re-submit for review
Preparing Your App
Protect customer data:
- Check profile permissions before ANY database action
- Review and defend any use of “without sharing”
- Use protected custom settings to store sensitive data
- Check for SHIELD-Encrypted Fields
Check for most common vulnerabilities:
- Search for script reflections
- Rename a record to and see what happens!
- Use a similar script in page input variables to ensure everything is encoded
- Protect your inputs: ensure any string-built queries aren’t vulnerable to injection.
- Verify field and object names against the schema
- Encode values to remove quotes
- Anything that might upset Lightning Locker
Prepare False Positives Document:
- List absolutely everything in the Checkmarx scan
- List all instances of Without Sharing
- List anything you think might raise questions
- Explain WHY you have chosen the implementation you did
- Is there a safer way to implement it?
Scan External Services and Applications:
- Use ZAP or Chimera to scan external services
- ZAP scans network traffic between you and an API
- Chimera performs a more thorough scan on services you control
- Test manually
- Don’t broadcast passwords unless required – use OAuth
- Don’t store passwords locally
- Always use HTTPS
- When in doubt: document it
Prepare a Test Environment:
- Use Environment Hub to create new org
- You won’t be able to use it after
- Review team will mess with data
- Create at least one user for review team
- Consider creating more users with various profiles
- Keep a user for yourself in case you need to go back
- Configure and populate with sample data
- Still unsure? Book time with Salesforce!
Submitting for Security Review
- Begin review from partner portal
- Fill in forms, upload documents
- Pay the fee (or not, if your app is free)
It’s a form – if you can’t do it, you have bigger things to worry about than security review ☺
Recording
Agenda
- So, You Want to Build an App…
- What is the Security Review?
- Why is the Review Important?
- How Does it Work?
- Preparing Your App
- The Review Loop
- Congratulations, You Passed!